Winter months bring the holiday season, but they also bring weather conditions that are more dangerous than any other time of the year. Working in cold conditions isn’t just uncomfortable, it can be dangerous. Frostbite, numbness, dehydration and hypothermia are real concerns for those working in outdoor weather. If you’re working outdoors this winter, be aware […]
Category: Uncategorized
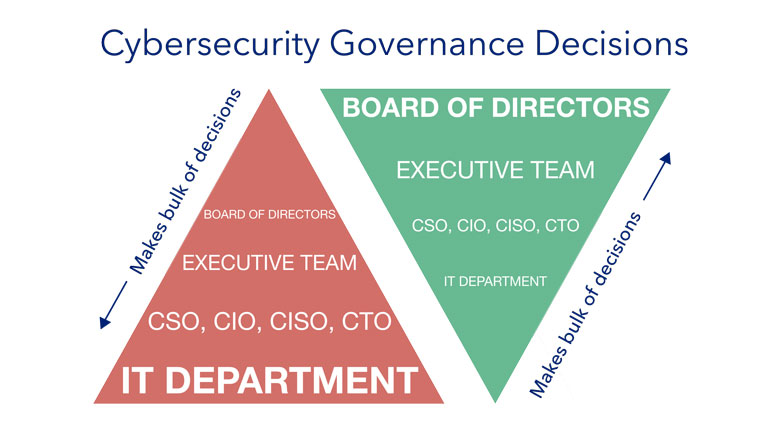
Healthy Cybersecurity Governance
Cybersecurity governance is an oft-neglected topic in organizations. It is often poorly understood because there is an aura of mystery around it. Many people convince themselves that they would never understand the technology, or it’s something “those IT guys” need to pay attention to. While it may require IT skills to fight it out in […]
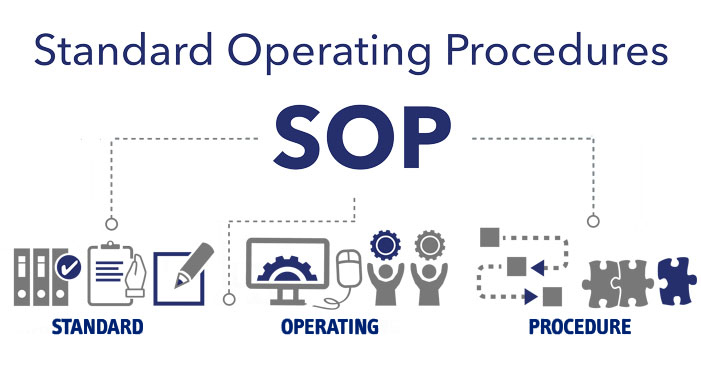
Know Your SOPs
Standard Operating Procedures (SOP) are a set of step-by-step instructions compiled by an organization to help workers carry out complex routine operations. SOPs aim to achieve efficiency, quality output, and uniformity of performance, while reducing miscommunication and failure to comply with specific instructions. SOPs and checklists are essential to the successful operation of our sites. […]
Google Says Phishing Attacks That Target Two Factor Authentication Are on the Rise. Here’s What You Can Do About It
For years, cybersecurity experts have tried to hammer the need for two factor authentication (2FA) into the minds of users. There’s a reason why. It is one of the most fundamental things one can do to protect digital assets. Yet, 2FA is not a panacea, and new phishing techniques show why. Recently Google has identified […]
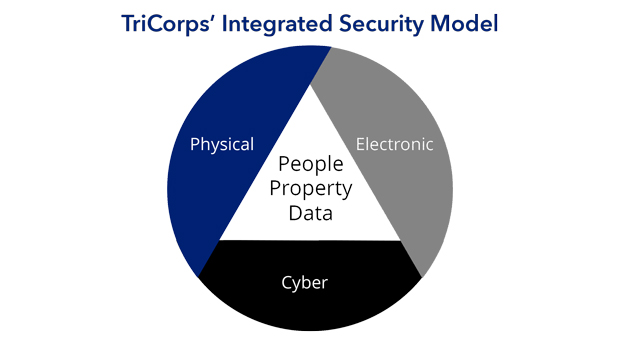
The Integrated Security Model: True Security
How secure is your office entry? How about your loading dock? Can you identify who inside your organization is disgruntled? What about outside? Who has been fired recently? Did they have access to sensitive files or IT property? When was the last professionally trained social media search of your company’s name? Industry? High level executives? […]