What is an Internal Cybersecurity Audit & Assessment?
An internal cybersecurity audit and assessment is concentrated on IT infrastructure, controls, and configurations within network boundaries to expose the internal weaknesses or insider threats. Consists of reviewing, assessing, testing, and reporting on your internal network infrastructure, including active directory and group policy security review, internal architecture review, and auditing of key services and applications.
Why are Internal Cybersecurity Audit & Assessments important?
Employees, contractors, and partners are essential to the operation of typical businesses. But what kinds of risk do you incur from the very people that are needed to operate your business? Organizations spend thousands, if not millions, of dollars purchasing the latest cybersecurity firewalls and intrusion detection systems to protect against external “threat actors.” Yet, they often turn a blind eye to one of the greatest threats to their organization’s data: people with direct and authorized access who are working within the organization.
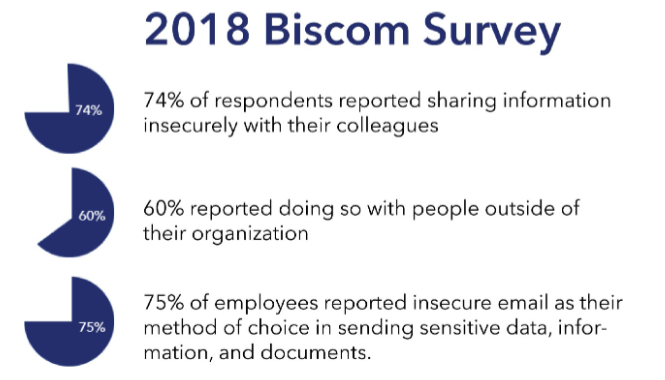
In 2018, Biscom, a maker of secure communications software, published a survey measuring the use of secure tools to share sensitive data, information, and documents. The survey found:
What We Provide:
Our consultants work collaboratively with your IT team to learn all of the aspects of your digital infrastructure and how it was configured. We use software tools that will study various aspects of your equipment in order to automate our ability to find hidden vulnerabilities. Our results are delivered in a detailed report that can help you build a remediation plan. We also provide an executive-level PowerPoint presentation that can be shared with team members and board of directors.
- Active directory structure and group policies review
- Internal architecture analysis
- Change/deletion auditing of AD, file servers, and SQL servers review
- Share and file system permissions assessment
- Search for interesting information (e.g. passwords, credit card info, etc.)
- Patches and configuration of servers assessment
- Patch management processes assessment
- Software development lifecycle assessment
- Vendor and partner integration and connectivity analysis
- WiFi implementation and security analysis
- Implementation and configuration of security tools review
- Change control review
- Incident response and reporting review
- Review of backup, business continuity, and disaster recovery plans for security deficiencies
- Employee training and testing review
- Mobile device management review
- Internet of things implementation evaluation
The results are securely delivered in a detailed report (Word Document) and an executive-level document (PowerPoint) so that a remediation plan can be developed.

