Most cybersecurity breaches do not come from vulnerabilities in the network, they come from employees who make a mistake. TriCorps’ employees are on the front lines of keeping the company safe from a cyber breach. That is why it is critical for you to learn what a cyberattack looks like and take steps to protect yourself and TriCorps from these types of attacks. First, let’s take a brief look at the most common types of cyberattacks:
Phishing: We all get phishing emails, every day. Traditionally, what comes to mind might be an email from a Nigerian prince willing to give you massive sums of his vast fortune if you only wire him a small loan. They have gotten way more sophisticated. Phishing emails now regularly include company branding, as you can see in the example. The goal of these types of emails is to cast a wide net and see who will take the bait. Phishing emails are designed to trick you into clicking on a link, downloading an attachment, or entering information (such as a username or password). They are cheap to make and distribute. Phishing emails do not include personalization and are not addressed to the recipient specifically. They also can include misspellings or links to dodgy web pages.
Spear phishing: These emails are much more personalized than phishing emails, although the goals are similar. They are specifically addressed to the recipient. They may include information about the recipient gained from information available online on the dark web, social media, and other websites, or gleaned from previous breaches. Spear phishing has become incredibly sophisticated. Attackers will craft emails that are spoofed to look like they are sent from someone a target knows and trusts or an organization a target regularly does transactions with (such as a bank or online retailer).
Business Email Compromise: This is a rising attack vector, one that is incredibly alarming. In it, an attacker sends an email to a target impersonating the target’s CEO and asking that person to quickly wire money on behalf of the organization. The victim fulfills the request and wires out the money to the attacker’s account. Once the money is wired, it is gone. The FBI estimates this type of attack has cost organizations billions of dollars.

Ransomware: A spear-phishing email is sent. The target clicks on a link or downloads an attachment. Suddenly a screen appears that alerts the target that his files have been locked down and they can no longer be accessed unless the target sends the attacker a ransom, usually in cryptocurrency. The rising value of cryptocurrencies, such as bitcoin, has helped fuel this type of attack.
These are just a few of the more common attack methods employed by actors in cyberspace. Hopefully, you are beginning to see a rhythm. One of the main ways that bad guys gain access is through a user clicking on a link or downloading an attachment. Therefore, it is imperative that you think before you click. If you are clicking on anything that is sent to you in an email or downloading any attachments, take a moment and consider if this is something you should be doing.
Email Intimacy: When we talk about emails, we like to use the analogy of a date. When you view an email, it’s much like sitting across from someone at a restaurant. But open an attachment or download a link and it gets a little more intimate:
Viewing an email will not cause you any harm. But anytime you go further by clicking or downloading, that’s when bad things can happen….
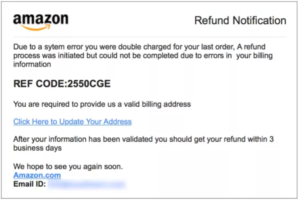
Guard Your Inbox: If you are sent an email, ensure that the sender is who they say they are. By adjusting a single letter (Amazon to Amaz0n), an attacker can spoof an email to make it appear to be a legitimate correspondence. If you’re not sure, pick up the phone. This is especially true if you’re asked to complete an action like clicking on a link, downloading an attachment, or entering credentials. If a company is asking you to reset your credentials, don’t do it from the email. Go to your web browser, navigate to their website, and change your information there. If a colleague asks you to complete an action, via email, and it feels strange, especially if it involves credentials or financial transactions, give them a call. Ensure the request is legitimate. It’s always better to be safe than sorry. Err on the side of caution.
Hover Before You Click: Before you click on a link, hover over it. A box will appear that will tell you where the link will take you. This way you can ensure that it is indeed taking you to the place it says it will take you. Do remember that attackers can spoof websites and email addresses by subtly changing letters to make the address seem like it is legitimate. Just be diligent.
Now we have to talk about passwords. If you’re like me, you hate passwords. We all do. They’re impossible to remember. It seems like everywhere you turn, you have to create a new password. One day, hopefully, we won’t need them anymore, but, for now, we are stuck with them. So, a couple of things about passwords.
Don’t Reuse Passwords: Never reuse passwords on multiple websites. Use a different password for each site. This is because if a password is compromised on one website, everywhere else that password is used is vulnerable.
Length and Complexity: You want to use complex passwords that are long (at least ten characters) and feature a combination of letters, numbers, and characters. The less complex the password, the easier it is to guess by a password cracker.
Consider a Password Manager: We all have too many passwords to manage mentally. We can’t juggle that much. Storing them on a device is dangerous, because if that device is compromised, so too are the passwords. Writing them down and stuffing them in a desk drawer may solve the problem of a cybercriminal gaining access, but it won’t stop a rogue colleague or wily janitor from scoring a motherload. A password manager can help safely store passwords. But make sure the password to your password manager is airtight.
Multifactor Authentication: Always…Always use multi-factor authentication. The most common example is when a website sends a PIN to your phone to allow you access to your account. Authentication methods are barriers to attackers. The more barriers you create, the less likely you are to be breached.
Update Your Software and Devices: Patch your software. Most software makes updating an effortless process now. We are all busy, and we avoid patching because it requires us to not have access to our software or devices for a brief period. Patches fix software vulnerabilities. When a company announces a patch, it is a clock to attackers. Until you patch, attackers know exactly the vulnerability they can use to attack your device or software. It’s wide open, until you patch. So, patch; do the update, grab a cup of coffee and bother your colleagues about your weekend plans. When you get back, your device will be much more secure.
That leads me to another important precaution. When you step away from your device, always lock the screen. Even if you are running to the break room for a cup of coffee or to ask a colleague a question, lock your screen. It only takes a moment for the right person to compromise you and the organization.
Don’t Overshare Online: We all like to share on social websites like Facebook, Instagram, and Twitter. But the information you share can be used to craft a targeted spear-phishing email. It can be used to guess your security questions on important websites like your banking website. This information can also be used to physically harm you or your loved ones. Some things to be wary of sharing:
- Your physical location
- Your work (especially in our line of work – security)
- The devices and software you use
- Details about your daily life
- Details of your friends and family
- Details about your purchases
You may want to consider making your social accounts private, so only those who you’ve accepted as friends can see your posts, leaving the rest of the world to wonder what you’re up to these days. We need you. TriCorps is under constant attack from cybercriminals who want to do our organization harm. We cannot keep TriCorps secure without your diligence. Please follow the advice contained in this column, and let’s be careful out there.

