How secure is your office entry? How about your loading dock? Can you identify who inside your organization is disgruntled? What about outside? Who has been fired recently? Did they have access to sensitive files or IT property? When was the last professionally trained social media search of your company’s name? Industry? High level executives? HR manager? These questions only scratch the surface of needed answers to fully and comprehensively guard against those that want to cause disruption, steal, harm, or settle a score. How vulnerable are you or your organization? Sadly, most never know until it’s too late.
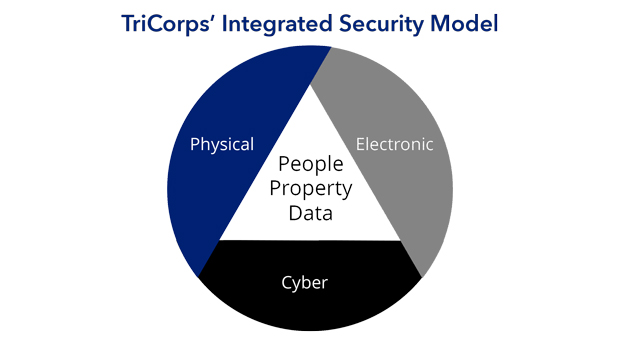
There are different elements to security: physical, electronic, and cybersecurity. In a vacuum one may appear sufficient, but if the goal is to fully protect people and assets, there is only model that provides true security.
Think about a few of the challenges in our culture. Workplace violence is on the rise. (No citation is needed here. Just Google ‘workplace violence.’) Yet seeing armed security guards in places of business is still the exception rather than the rule. How many times have we heard, “our number one asset is our employees?” If that is true, then true security measures should be implemented and integrated. The majority of workplace violence takes place at known soft targets. A researcher would be hard pressed to find the incident where an orchestrated attack was successfully executed on a target that was hardened physically, electronically, and technologically.
Data breaches are commonplace among governments and IT companies. While simultaneously, contracts for cyber audits or IT consulting attempting to “protect” highly sensitive personal or company information are too often awarded to the lowest bidder. In the private sector, executives commonly ask their IT departments to perform beyond their scope or capabilities given work-day time constraints. In government, the recognition for a job well done is draped in “saving the taxpayer money.” Time and again taxpayers’ money has been saved while their social security numbers, identities, military data and retirement information has been breached. Most taxpayers would prefer government spend a little more and protect them a lot better.
Time and time again, after-incident investigations reveal perpetrators forecasted their evil intent, malicious desires and potential targets via a social platform. However, there is still a void in surveilling social media in the private sector. The majority of companies and private citizens have no time or level of expertise to adequately monitor social media tools for intel that could lead to mitigating harm to people or assets. As true as that may be, it is still a lost opportunity.
How do you truly protect what you care about most? The integrated security model encompasses comprehensive aspects of physical, electronic, and cybersecurity. There is a very simple reason to re-examine and address personal and company security. The world isn’t getting any safer. As equally unfortunate, the targets of bad guys aren’t getting any more secure. Just for the sake of clarity: Who or what are the targets of bad guys? Simply put: You and your information. You are a target personally, and where you work is a professional or commercial target. There are countless concerns and vulnerabilities that go largely undetected until it’s too late. It is time to accept the reality that there are many levels of bad people in the world that have the capability to harm you technologically, digitally, professionally, personally, and possibly physically. Hackers, organized crime, gangs, terrorists, disgruntled employees, fired former employees, foreign governments, and the ‘nicest guy in the world’ who had decided to stop taking his prescription that makes him the ‘nicest guy in the world’. That harm could meet you or your company very purposefully or randomly. Either way, it’s better to have a full-scaled integrated security system in place and avoid victimization.
No one; no company readily admits neglect of security measures. However, just because a company has security does not mean they are secure. Right now, someone is reading this article and thinking, “well, we do that.” You might do some of that, but you don’t do all of that. Hardly anyone does. There are roughly three groups that think of and practice fully integrated security: A few elite government entities; a select group of publicly traded companies that take their fiduciary duties seriously; and small companies and schools that have fallen victim to violence vowing to never allow it to happen again. Too often money or budget is a reason for not implementing security when, in actuality, protecting people and assets is sometimes less expensive than a utility or insurance payment. The three groups above addressed the cost issue to implement fully integrated security. They realized they could not afford not to. What is the greatest asset to your company?